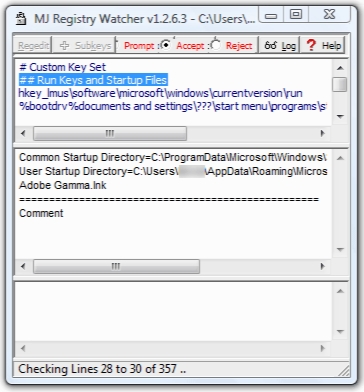
MJ Registry Watcher 1.2.8.6
- نسخه :Version 1.2.8.6
- نوع فایل : نرم افزار
- زبان : انگلیسی
- سیستم عامل : Windows 32 & 64 Bit
- تولید کننده : Mark Jacobs
- سال تولید : 2018
Description
MJ Registry Watcher is a simple registry, file, and directory hooker/poller, that safeguards the most important startup files, registry keys and values, and other more exotic registry locations commonly attacked by trojans.
It has very low resource usage and is set to poll every 30 seconds by default, although you can adjust this to anywhere between 0 and 9999. A configuration file stores all your settings for future use. MJRW not only polls the system, but it also hooks it, so that most changes to keys, files and directories are reported instantaneously. Key deletions are still caught by the polling loop though since they cannot be hooked. Exactly which keys and files are protected can be completely configured by the user, although the sets I supply with MJRW will cover most standard PCs.
To install it, extract the files with pathnames, and you'll have a self-contained .exe file with a small help text file, the keys and files lists, and a couple of exclusion files in the MJRegWatcher directory. Create a shortcut to C:MJRegWatcherRegWatcher.exe and launch it. Then, use the Options, Settings, Automatic Startup Options screen to install it either just for the current user or for all users. From this screen, you can also choose which key set to start it up with, or even uninstall it. Please note that under Vista, MJRW will need to be configured with Administrator privilege to write to the registry. To do this, go to the RegWatcher.exe file in Explorer, right-click to Properties, and go to the Compatibility tab. Check the admin box. Whenever the Vista PC is restarted, you will have to OK MJRW to start with admin rights. Unless you disable UAC, the only way around this is to use the task scheduler to launch MJRW with administrator rights and set it to run at logon.
If a trojan attempts to change your startup settings, you will be alerted, and you can prevent any changes being made. You can also configure MJRW to email the alert details to, for example, an administrator. It is fully configurable as to what keys and files are monitored. So, if you have a vested interest in protecting your file association for the mailto protocol (your default emailer), so that your preferred app loads them, and something else is trying very hard to undermine this association (Outlook for example), this will pop up, offering to stop a new association attempt, after Outlook had loaded, say. The key that stores this association is hkey_lmussoftwareclassesmailtoshellopencommand, and you could protect other associations by changing "mailto" to the desired type, for example, "jpegfile."
It assumes write access and directory create rights for the path the .exe file sits in (i.e. wherever you installed it). The default set of keys and files should ensure that nothing gets run at startup without you knowing about it, and important bootup files don't get changed behind your back. When monitoring, keys are opened in Read-Only mode, and the application only needs 'Write Registry' access when it has detected a change. It keeps a log of any suspicious activity and displays any such information for the current session in the bottom panel. A log file has this appended to it and can be viewed by pressing the Log button. The file keeps a complete history of alerts.
It has very low resource usage and is set to poll every 30 seconds by default, although you can adjust this to anywhere between 0 and 9999. A configuration file stores all your settings for future use. MJRW not only polls the system, but it also hooks it, so that most changes to keys, files and directories are reported instantaneously. Key deletions are still caught by the polling loop though since they cannot be hooked. Exactly which keys and files are protected can be completely configured by the user, although the sets I supply with MJRW will cover most standard PCs.
To install it, extract the files with pathnames, and you'll have a self-contained .exe file with a small help text file, the keys and files lists, and a couple of exclusion files in the MJRegWatcher directory. Create a shortcut to C:MJRegWatcherRegWatcher.exe and launch it. Then, use the Options, Settings, Automatic Startup Options screen to install it either just for the current user or for all users. From this screen, you can also choose which key set to start it up with, or even uninstall it. Please note that under Vista, MJRW will need to be configured with Administrator privilege to write to the registry. To do this, go to the RegWatcher.exe file in Explorer, right-click to Properties, and go to the Compatibility tab. Check the admin box. Whenever the Vista PC is restarted, you will have to OK MJRW to start with admin rights. Unless you disable UAC, the only way around this is to use the task scheduler to launch MJRW with administrator rights and set it to run at logon.
If a trojan attempts to change your startup settings, you will be alerted, and you can prevent any changes being made. You can also configure MJRW to email the alert details to, for example, an administrator. It is fully configurable as to what keys and files are monitored. So, if you have a vested interest in protecting your file association for the mailto protocol (your default emailer), so that your preferred app loads them, and something else is trying very hard to undermine this association (Outlook for example), this will pop up, offering to stop a new association attempt, after Outlook had loaded, say. The key that stores this association is hkey_lmussoftwareclassesmailtoshellopencommand, and you could protect other associations by changing "mailto" to the desired type, for example, "jpegfile."
It assumes write access and directory create rights for the path the .exe file sits in (i.e. wherever you installed it). The default set of keys and files should ensure that nothing gets run at startup without you knowing about it, and important bootup files don't get changed behind your back. When monitoring, keys are opened in Read-Only mode, and the application only needs 'Write Registry' access when it has detected a change. It keeps a log of any suspicious activity and displays any such information for the current session in the bottom panel. A log file has this appended to it and can be viewed by pressing the Log button. The file keeps a complete history of alerts.
برای اطلاع از طریقه نصب به فایل How to Install.txt رجوع شود.